Yes, you’ve read it right: a critical, unpatched 0-day vulnerability affecting WordPress’ comment mechanisms was disclosed earlier today by Klikki Oy.
Who’s affected
If your WordPress site allows users to post comments via the WordPress commenting system, you’re at risk. An attacker could leverage a bug in the way comments are stored in the site’s database to insert malicious scripts on your site, thus potentially allowing them to infect your visitors with malware, inject SEO spam or even insert backdoor in the site’s code if the code runs when in a logged-in administrator browser.
You should definitely disable comments on your site until a patch is made available or leverage a WAF to protect your site and customers.
Technical details
This vulnerability requires an attacker to send a comment long enough to force the backend MySQL database to truncate what is stored.
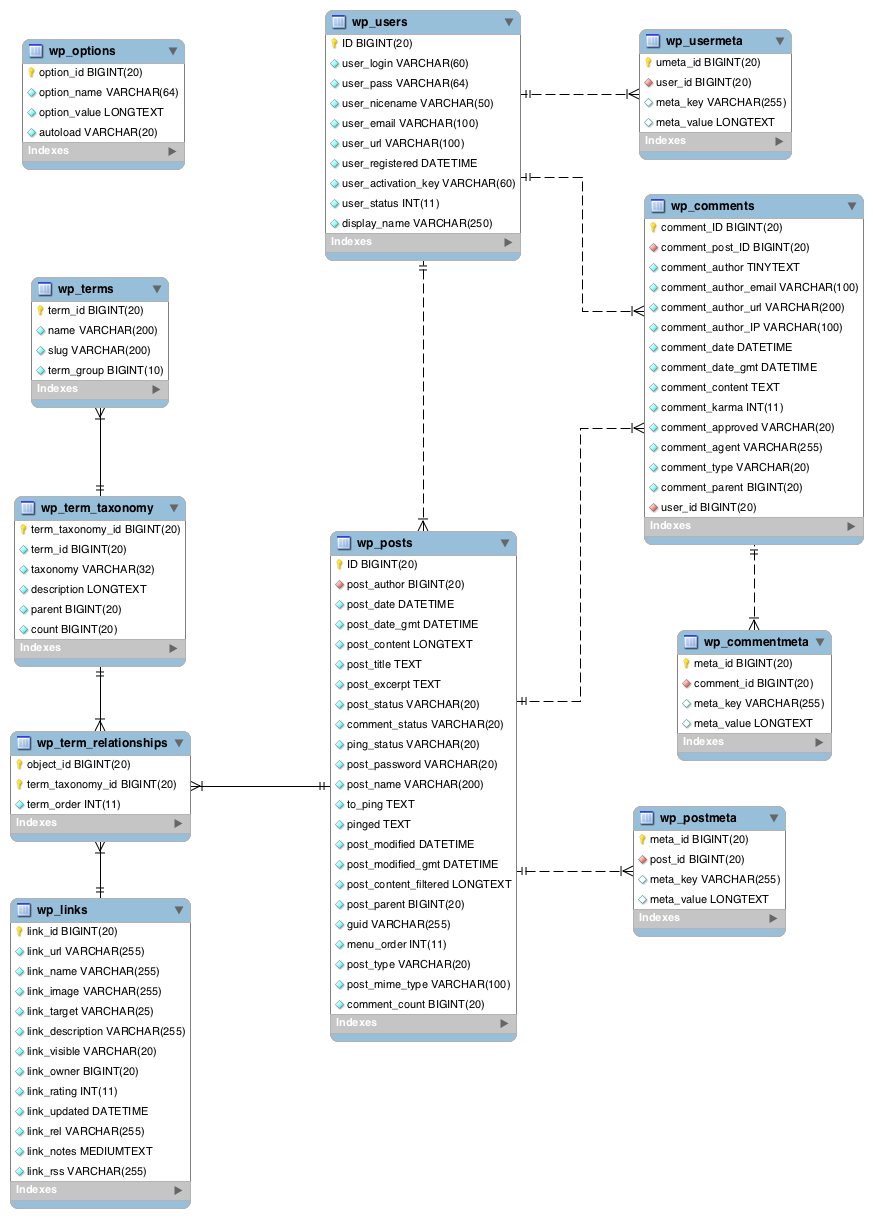
WordPress Database Schema
As you can see from the above schema, the comments texts are stored in the comment_content column which is a TEXT column, meaning a comment can only contain a maximum of 65535 bytes of data.
A typical exploit would look like the following:
<a href='x onclick=alert(1) AAAAAAAAAAAAAA..(multiplied so our comment contains more than 65k bytes)'>test</a>
Once taken back from the database would look like this:
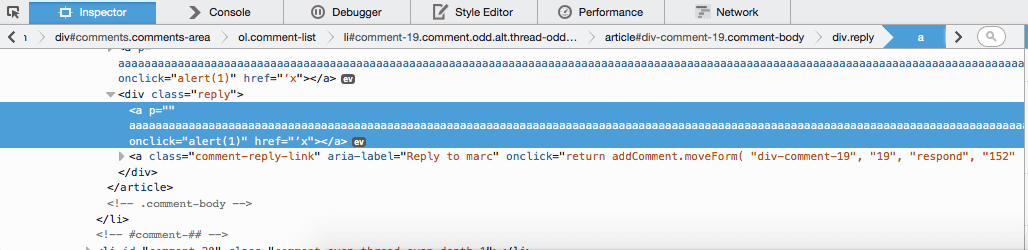
<p><a href='x onclick=alert(1) AAAAAAA</p>
Some of you might have noticed that the resulting HTML tag isn’t complete, but this isn’t a problem for most modern browsers as most of them will simply patch it up automatically:
This bug then allows anyone to insert any HTML tag attributes to his hyperlink, including Javascript event handlers.
.png)
 By
By
 05:53
05:53








0 yorum